

In our modern world, Ethernet and TCP/IP have become the de facto standards in most mission-critical control and monitoring applications, largely due to the design of these protocol suites around the Open System Interconnect (OSI) model. However the freedom and flexibility of being built around such an open system philosophy, while playing a large part in the success of Ethernet, also allows for many vulnerabilities which can be exploited by attackers.
Cybersecurity has become the greatest driving factor when designing and maintaining these networks, even more so than reliability and availability.
In planning and designing cybersecurity for a mission-critical network, a common mistake is to see the network as a single entity, and simply try and protect this entity holistically. While this view is not completely wrong, it is not the only perspective that should be taken when designing such a security system. Instead we should approach cybersecurity from a more granularly, and as the OSI model is already a well-developed and understood reference, we can use this to guide our approach.
We start at the base of the model by considering physical security. A mission-critical site should already be very familiar with physical security considerations such as access control to certain areas, and layered access control with areas like control rooms being extra secure. Networking hardware should be either contained in cabinets in the control room, or in locked cabinets out in the plant/field, with only certain engineers and technicians having access. Cables will generally already be run in to reach locations such as trenches, or along ceilings. Preventing access to cables was more important when backbones consisted of copper cabling, which is much easier to tap into without disrupting the network. Even fibre cable can potentially be cut and spliced into tapping equipment, but this requires more specialised hardware and longer periods of access to cabling, and is more detectable. At least the initial cut of the cable will definitely be more easily detected, and so is not as much of a security concern.
Next we look at layer 2, or our switching level. In most cases, our layer 2 network is considered ‘secure’, as it generally falls completely within the site’s physical and logical areas, and we normally focus on security at the edges/perimeter of a network. Historically we have not worried much about authentication or encryption at layer 2. However these days even this is being re-evaluated in most cases, especially with layer 2 fibre networks often now spanning public access locations. Layer 2 MAC authentication between ports is something being introduced by many vendors. Previously port security was more about protecting edge ports against unknown connections, but now this is expanding to make sure that links between two switches on the network are indeed between those two switches, and not going via some ‘man in the middle’ type attack. Links have to constantly ensure this authentication is real, otherwise they will be disabled until they can correctly authorise the switch.
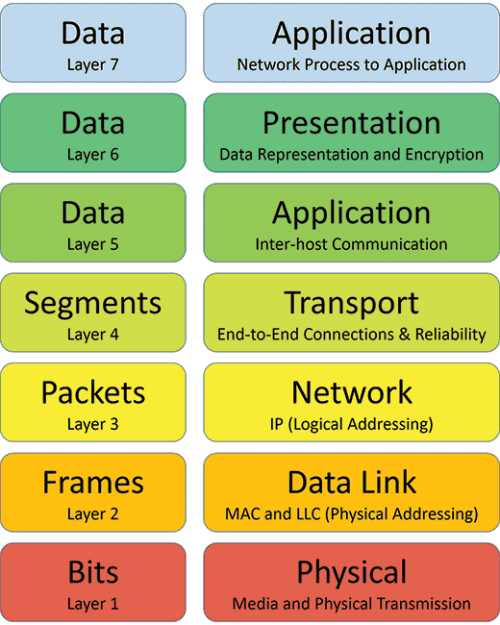
However, a much more common functionality exists at layer 2 that is ubiquitous in industrial sites, and helps with not only security, but load balancing and determinism as well, namely Virtual Local Area Networks (VLANs). In corporate-type environments VLANs are generally not used, and IP subnetting is the primary way of segregating logical network segments. However, IP subnetting does not actually stop certain packets from one subnet from reaching a device in another subnet, and can be exploited to spread malware. VLANs, on the other hand, are defined and managed by the switches themselves, meaning that data in one VLAN that we do not want to reach a device in another VLAN, will not be able to do so unless we specifically allow it. This means that the end devices are much safer, and an attack or issue within one VLAN is not as easily transferred into another VLAN. This is why we also often implement guest or contractor VLANs to allow control over third-party access when working on the network.
We can look at layer 3 and 4 together, as these are generally secured using integrated firewalls, which look at the layer 3 and 4 headers of the traffic (and in some cases even more layers, especially with newer firewalls).
Firewalls generally exist in one of two fashions, or both in many cases. The first is a gateway or layer 3 switch between two logical network segments. Normally we consider one of these to be unsecure, or at least less secure than the local network we are in charge of. The second is a router-on-a-stick, where the router is connected just on the edge of a network, and handles routing between IP subnets and VLANs within that network specifically. However, in both cases the operation of the firewall is the same.
Although different vendors approach the operation of a firewall differently, the basic premise is the same. Firewalls will divide the network into logical portions or zones, and will then be able to control traffic attempting to move between these zones using the router. This control will generally be achieved by creating a list of rules that define how to treat packets of different types. For instance, it might define a source IP address or range, meaning packets from those devices are subject to this rule. At the end of the list of rules will be a catch-all rule, which should always be configured to drop all packets, except sometimes for testing. This means any packet that we have not specifically created a rule for in order to allow it through the firewall will be stopped and discarded. In this way we are able to control the traffic entering and leaving the network.
Virtual private networks (VPNs) are another buzzword these days, and for good reason. A VPN is a way of creating a secure tunnel through an unsecured network, meaning that even traffic that is not natively encrypted will be placed into the tunnel and encrypted at a higher level. To the end devices and processes this will be completely transparent, but it will stop any attacker from reading the traffic as it passes through the unsecure network portions. In mission-critical networks, especially in South Africa where many sites are running hardware more than ten years old, this functionality can become extremely important when hardware suppliers need to log in remotely to the devices for maintenance or troubleshooting. Many of these devices may not natively support encrypted protocols such as SSH, and instead may use an open protocol like Telnet to communicate. In these cases the unsecure Telnet traffic will at least be encrypted while travelling across unsecure network portions.
In recent years we have started to see the introduction of Intrusion Detection Systems and Intrusion Prevention Systems (IDS/IPS) and Next-Generation Firewalls (NGFWs). The full scope of these is beyond the time we have here, but suffice to say that these systems are starting to add more intelligence and decision-making capabilities to the hardware itself using AI. IDS systems will use pattern tracking to create baselines of the traffic on the network, and will then notify administrators on anomalies to these patterns, allowing the administrator to take manual action to prevent an attack, or deal with an issue before it becomes too serious. An IPS takes this one step further. While it will still notify the admin of anomalies, it will also be able to take active steps to prevent the anomaly, such as sending a command to a NGFW to add or edit a rule to disallow that traffic. At the same time the administrator will still be notified, so the changes can be confirmed or denied.
While we could go on for hundreds of pages on the intricacies of cybersecurity, it is important to note a couple of things. Firstly, while it is important to look at the overall system holistically, it is just as important to look at the smaller details when designing a cybersecurity approach, and consider each possible avenue of attack on the network. Secondly, security is a constantly changing field, and as such must be constantly re-evaluated and added to. However, at the same time, we must consider the third point, that security is not a way to completely block attacks, but rather a deterrent. Any system built by people is fallible, and generally can be exploited. As such we must constantly rethink our own security, and never get caught in the trap of thinking that our networks are ever truly 100% secure.
| Tel: | +27 11 454 6025 |
| Email: | [email protected] |
| www: | www.h3isquared.com |
| Articles: | More information and articles about H3iSquared |

© Technews Publishing (Pty) Ltd | All Rights Reserved