Trojan uses LiveCD for Android running on x86 platforms as bait
June 2010
IT in Manufacturing
With the growing interest in testing the new Android OS on x86 platforms, cybercriminals are looking to exploit vulnerable users wanting to install the operating system on their PCs. A piece of malware is hosted by a fake webpage, imitating the original Android LiveCD one, and offering the 'hunted' software.
In essence, Google Android is a Linux kernel-based operating system for mobile phones. The statistics published on different Android-related sites and mobile advertising networks reflect its success worldwide:
* About 60 000 Android phones are sold daily and about 22 000 000 a year.
* Android Market delivers over 30 000 Android Apps.
* About 60% of Android Apps are free.
* 167 Apps have been downloaded between between 667 000 and 2,9 million times.
* The average paid Android app is priced at $3,27.
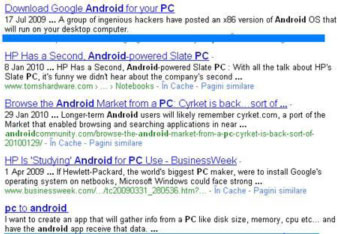
Android-powered Netbooks have recently appeared on the market, meaning that Android OS can now be installed on Netbooks and, of course, on normal PCs. A quick search on the Internet for 'Android on PC' and, here it is: a long list of sites offering the possibility to test the new OS on x86 Windows platforms.
Figure 1. Results for 'Andoid on PC' Internet search
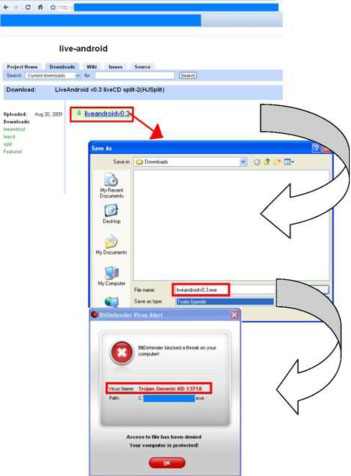
An apparently unsuspicious link in the returned list of results, one click, and the user is redirected to a look-alike of the LiveAndroid page, which, instead of the promised OS for PCs, delivers a Trojan.
Figure 2. Trojan instead of Android OS
Identified by BitDefender as Trojan.Generic.KD.13718, this piece of malware affects only Windows platforms and contains malicious or potentially unwanted software which it drops and installs on the system. Frequently, it installs a backdoor which allows remote, clandestine access to the infected system. This backdoor may then be used by cybercriminals to upload and install additional malicious or potentially unwanted software on the captured system.
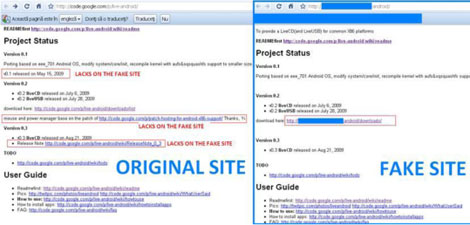
A closer look at the fallacious site and at the downloaded file reveals several differences, the most important of which being that the downloaded file should have an .iso image, not an .exe extension. The sites may look the same, but there are a few minor details that will set the bogus apart from the genuine one (as indicated in the screenshots below):
Figure 3. Original Live Android site vs. Fake Live Android site
In order to stay safe, BitDefender recommends you to install and update a complete antimalware software solution on your system.
Other details about this malware alert:
For more information contact: Alina Anton, senior PR and marketing coordinator, EMEA & APAC Business Unit, BitDefender, +40 212 063 470, [email protected], www.bitdefender.com
Further reading:
South Africa’s AI revolution is here – but are we secure?
IT in Manufacturing
South African businesses are sprinting to embrace generative AI, lured by its potential to drive efficiency, productivity and innovation. But here’s the stark reality: without a rock-solid cybersecurity foundation, AI will become a Trojan horse, opening the floodgates to sophisticated cyber threats.
Read more...
Black Rock Mining centralises mining operations with AVEVA
IT in Manufacturing
Black Rock Mine Operations replaced and upgraded its existing infrastructure, and installed additional capacity to expand production from 3 to 4,6 million tons in three years. The new system is powered by a suite of AVEVA solutions.
Read more...
Shaping data resilience strategies with AI and hybrid cloud solutions
IT in Manufacturing
In today’s rapidly evolving digital landscape, organisations are under growing pressure to secure their operations against increasingly sophisticated cyberthreats, including those that leverage AI to enhance the success rate of attacks. In this landscape, it has become essential to ‘fight fire with fire’ – harnessing AI as a means to counter these threats.
Read more...
Cloud or on-prem? Decoding the choices for South African enterprises
IT in Manufacturing
The debate between on-premise and cloud computing architectures remains a prominent topic among businesses, particularly in South Africa.
Read more...
Advancements in wire rope testing
IT in Manufacturing
Being able to get instant, real-time and portable detection of wire rope flaws can make a significant difference for operational teams. There have been a number of significant technological advancements and tools entering the market that help wire rope operators detect and resolve problems faster.
Read more...
Quantum computing power: four steps to protecting your business
IT in Manufacturing
Are you ready for Q-day? Post-quantum cryptography isn’t just an IT issue, it’s a business continuity concern. Quantum computing is fast becoming a reality.
Read more...
Schneider Electric relaunches legacy access control systems
Schneider Electric South Africa
IT in Manufacturing
Schneider Electric South Africa has relaunched its comprehensive access control platform to help customers upgrade from ageing and obsolete systems.
Read more...
Digitalisation in mining - the advantage you need now
Schneider Electric South Africa
IT in Manufacturing
Digitalisation offers immense and proven benefits such as streamlining operations, reducing error and accelerating workflows. Mining operators today leverage digital technologies to improve efficiency, sustainability and very importantly, safety.
Read more...
The shape of water – automating hydropower operations
Schneider Electric South Africa
IT in Manufacturing
Hydropower is undoubtedly one of the building blocks of today’s renewable energy industry and its operations need to be efficient, reliable and sustainable. Automation must therefore form part of today’s modern hydropower operations to improve resource management and enhance reliability.
Read more...
What lies beneath – the hidden cost of AI
Schneider Electric South Africa
IT in Manufacturing
The world is quickly realising that with the rapid advancement in AI there are also caveats. In short, apart from environmental implications, it also has major significant financial ramifications.
Read more...