

One aspect of unplanned downtime that is coming into focus is that caused by breaches in control system security. The problem is best addressed by ensuring physical site security is adequate, correct system security procedures are in place and control system operators and engineers are properly trained.
Modern digital automation systems, for reasons of lower cost and interoperability with other plant systems, are now using commercial off-the-shelf (COTS) hardware and software components that make these systems more open to attack by viruses, hackers and worms. Downtime can be caused maliciously or inadvertently by the introduction of viruses. Hackers can cause downtime or if they were so inclined could take control of the plant, causing equipment damage or more severe consequences.
Control system manufacturers must therefore build security into their systems but are often unwilling to discuss exactly what they build in and how it works as this would defeat the objective.
Security can be approached in two ways, reactive and proactive. Reactive security merely ensures that should an attack take place the system will deal with it and prevent it causing a problem. Reactive measures include hardening a controller to survive an attack, the use of anti-virus software and intrusion detection systems. Proactive security, on the other hand, tries to remove the possibility of there being an attack in the first place. Proactive security entails such things as correct installation of the network, the use of firewall devices to prevent access, preventing physical access to equipment and ensuring the proper security procedures are in place and are followed.

Proactive measures
To ensure any control network remains secure from attack, whether deliberate or not, there are several elements that must be in place. The first of these elements is ensuring the control network is isolated from the plant LAN or any other open LAN. An easy way to achieve isolation would be to make no physical connection to the control network at all. However in these days of asset optimisation, the control system vendors are making it even easier for their systems to communicate with other systems such as asset management systems (AMS), computerised maintenance management systems (CMMS) and enterprise resource planning (ERP) systems. Without a connection to the plant LAN the benefits that these capabilities offer are lost.
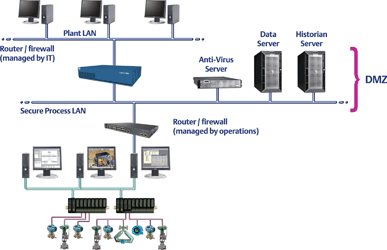
Ideally a control LAN would be configured as a dedicated, isolated network with very defined and regulated methods of connection(s) to other LANs. A preferred connection method is to create what is called a demilitarised zone (DMZ) by employing a router/firewall device between the LANs and in addition making all external connections through a workstation on the control LAN (see Figure 1). In this configuration the workstation acts as a neutral zone between the control network and the plant network. It prevents plant users from getting direct access to the devices on the control network.

Another element that contributes to overall system security is physical access prevention. Good security practice dictates that controllers and network equipment are installed in locked or sealed enclosures that prevent easy access by unauthorised personnel. This is to prevent access by unplugging a network device and using this cable for access, or simply plugging into an unused port on a network device. Wherever possible unused network ports should be disabled in the configuration of the device and network cabling should be protected from easy access.
The most reported method of introducing a virus has been users introducing them by using infected media to copy files to a workstation. To prevent this, drives should be disabled or unplugged to prevent users from introducing viruses and other malware programs into the system. Similarly, USB ports (except those actually in use) should be physically disconnected so they cannot be accessed by unauthorised users who may be tempted to transfer data using a USB memory device. In addition, since most virus and malware is spread via e-mails and Web access, control system workstations should never provide e-mail access or have the ability to make a direct connection to the World Wide Web outside the plant. If it is required for operators to access e-mail or the Internet then separate computers, not connected to the control system LAN, should be used for these applications.
Access to the control room should be controlled at least to the extent that the personnel in the room are policing access to the workstations. In the case of remote consoles located away from the control room, procedures should dictate that operators log out or lock consoles when not actively in use. Remote workstations themselves should be setup so that they automatically lock the screen after a very short period of inactivity. Typically, a two minute delay would be recommended.
User access security is probably the most important but mismanaged aspect of security. It is important to properly manage the system users if any level of security is to be achieved. Access should only be granted to those individuals who perform system functions and the user list must be actively managed to delete users who no longer should have access to the system. For users who require only process data access, provisions should be made to locate the information on a separate data server located away from the control system functions in a secure process LAN acting as a DMZ (see Figure 2). In addition there should be role-based security allowing users access only to those elements of the control system that are necessary for them to perform their function.
There has been a lot mentioned about firewalls, as a firewall examines all traffic routed between the control network and the plant LAN to ensure that it meets certain criteria. If it does, the data is routed between the networks, otherwise it is stopped. Firewalls must be configured for the application. Firewalls can perform address and protocol filtering to ensure that only certain computers can access the system, via certain port numbers or that certain protocols such as HTTP are restricted from accessing the network. Most control systems will use specific ports for communications and all other ports should be closed or disabled to prevent connections being made through other open ports.
The above proactive measures should prevent unauthorised access to your control network and the introduction of potentially harmful viruses and malware; however they do depend on adherence to procedures. In order for these measures to remain effective they should be continually and thoroughly policed and amended as necessary. Should these procedures fail then there is still the potential for problems, this is where reactive security measures should be adopted.
Reactive measures
Anti-virus software screens files moving in and out of the network to ensure that there are no viruses present. The most common delivery method for viruses is via e-mail attachments, hence the stipulation that control system workstations should not be configured to accept e-mails. Another common means of delivering viruses is in a document downloaded from the Internet. Anti virus software will detect viruses, no matter how they are brought in. This is dependent on the anti-virus software being kept up-to-date as new viruses are being developed all the time.
Intrusion detection systems will monitor all access attempts and allow users to detect inappropriate, incorrect, or anomalous activity that takes place on a network. An intrusion detection system requires frequent review of the communication logs to discover if attempts have been made to hack into the system or if users are making frequent attempts to access areas where they are not normally permitted. Intrusion detection activities can be labour intensive and are best deployed in high security situations where the cost to monitor can be justified.
Summation
Basic system security is relatively straightforward and most elements can be implemented by a plant or process engineer. The proactive elements include physical security of system hardware, network security using routers and firewall devices in a DMZ configuration and enforcing user access. Reactive security elements include the monitoring of access logs and maintaining anti-virus software. These basic measures can go a long way to protecting control systems from hacking and viruses.
For more information contact Widad Haddad, Emerson Process Management Dubai, +971 4 883 5235, [email protected], www.emersonprocess.com
| Tel: | +27 11 451 3700 |
| Fax: | +27 451 3800 |
| Email: | [email protected] |
| www: | www.emerson.com |
| Articles: | More information and articles about Emerson Automation Solutions |

© Technews Publishing (Pty) Ltd | All Rights Reserved